Azure Single Gateway Deployment
This Terraform configuration creates a basic Azure networking setup with an Enforza server acting as a gateway/router for private subnets.
Architecture Diagram
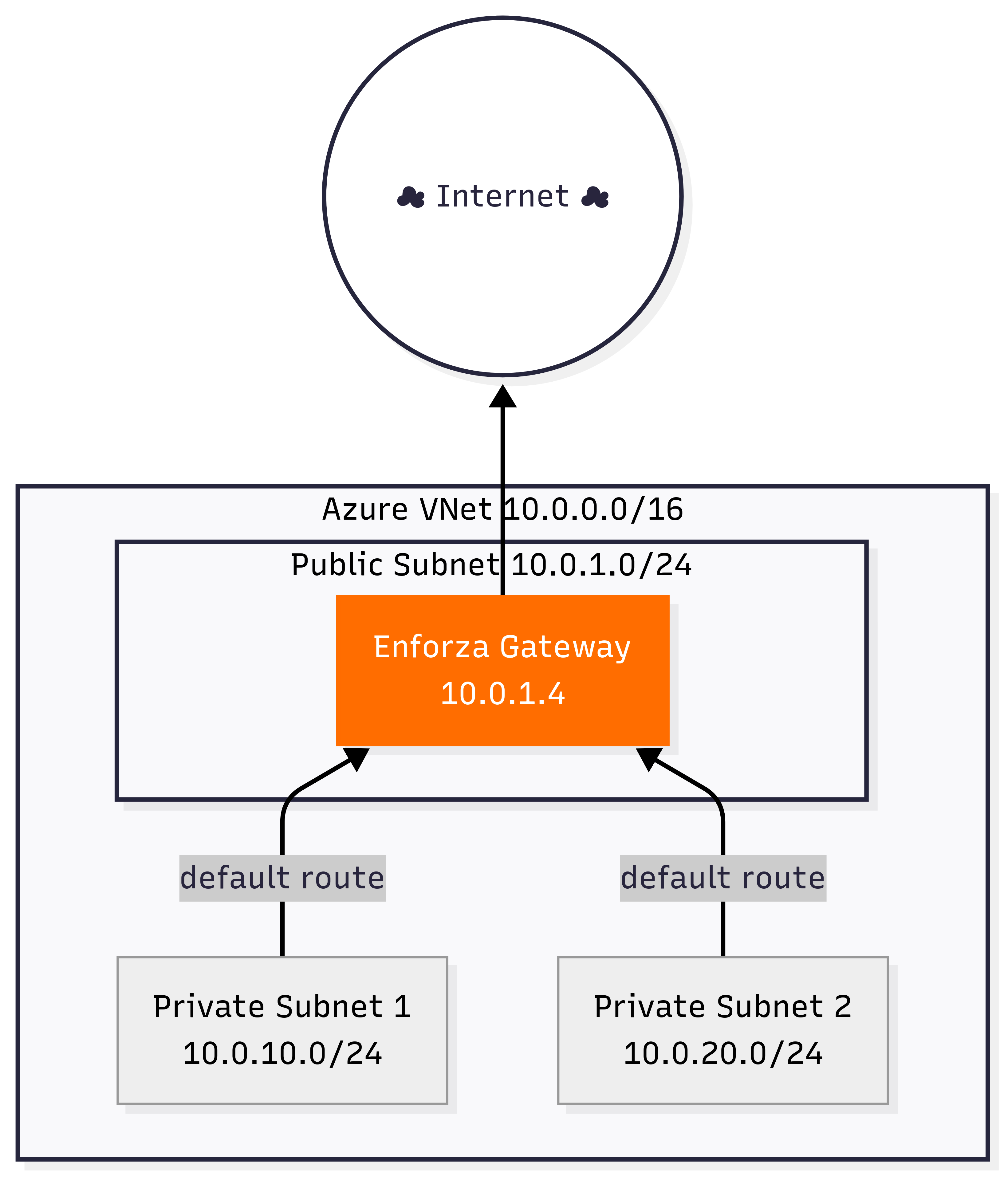
Components Created
Network Infrastructure
- VNet: 10.0.0.0/16 address space
- Public Subnet: 10.0.1.0/24 (contains Enforza gateway)
- Private Subnet 1: 10.0.10.0/24 (routes via gateway)
- Private Subnet 2: 10.0.20.0/24 (routes via gateway)
Enforza Gateway Server
- VM: Standard_B1s Ubuntu 22.04 LTS
- Role: Router/Gateway
- IP: Static 10.0.1.4 (private) + dynamic public IP
- Security: NSG with "permit any any" rules
- Features:
- Enforza agent automatically installed, and registers to the Enforza Cloud Controller
- Routes traffic from private subnets to internet via Enforza gateway
Route Tables
- Private Subnets: Default route (0.0.0.0/0) → Gateway (10.0.1.4)
- Internet Access: Private subnet VMs route through gateway for outbound
Quick Start
-
Clone the repository and navigate to the Azure Single AZ directory:
git clone https://github.com/enforza/azure-terraform.git
cd azure-terraform/simple-single-az -
Authenticate to Azure:
az login -
Configure variables:
cp terraform.tfvars.example terraform.tfvars
# Edit terraform.tfvars with:
# - Your subscription ID
# - Your Enforza company ID
# - Authentication method (password or SSH key) -
Deploy:
terraform init
terraform plan
terraform apply -
Manage via the Enforza Cloud Controller:
The device will have automatically registered itself in the portal. Login, and under devices, you should see a newly provisioned device with no name.
Configure a name, associate with a policy, and push!
Authentication Options
Choose ONE method in terraform.tfvars:
Option 1: Password Authentication
admin_password = "YourSecurePassword123!"
Option 2: SSH Key Authentication (Recommended)
ssh_public_key = "ssh-rsa AAAAB3NzaC1yc2E... your-key-here"
Enforza Company ID
enforza_companyId = "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"
You can get your enforza_companyId from the Enforza Cloud Controller portal here and navigating to "Profile" and copy/pasting Company ID.
Usage Examples
Deploy Private VMs (Optional)
After creating the gateway, you can deploy VMs in the private subnets. They will automatically route internet traffic through the gateway:
# Example: Add to main.tf to create private VM
resource "azurerm_network_interface" "private_vm" {
name = "private-vm-nic"
location = azurerm_resource_group.main.location
resource_group_name = azurerm_resource_group.main.name
ip_configuration {
name = "internal"
subnet_id = azurerm_subnet.private_1.id # or private_2
private_ip_address_allocation = "Dynamic"
}
}
Monitor Traffic
SSH to the gateway and monitor routing:
# Watch traffic flowing through gateway
sudo tcpdump -i any -n host 10.0.10.0/24 or host 10.0.20.0/24
# Check routing table
ip route show
Test Connectivity from Private VMs
# From a private subnet VM (once deployed)
curl ifconfig.me # Should show gateway's public IP
ping 8.8.8.8 # Should work via gateway
Cost Estimate
Monthly cost: ~$25-35 (UK South region)
- Standard_B1s VM: ~$15-20/month
- Storage (Premium SSD): ~$5/month
- Public IP: ~$3/month
- Networking: ~$2-7/month
Customization
Change VM Size
vm_size = "Standard_B2s" # More powerful
vm_size = "Standard_B1ls" # Even cheaper (burstable)
Modify Network Ranges
vnet_address_space = ["192.168.0.0/16"]
public_subnet_prefix = "192.168.1.0/24"
private_subnet_1_prefix = "192.168.10.0/24"
private_subnet_2_prefix = "192.168.20.0/24"
Troubleshooting
Can't SSH to gateway?
- Verify NSG rules allow SSH (should be "permit any any")
- Check authentication method matches terraform.tfvars
- Ensure public IP is assigned:
az network public-ip show
Private VMs can't reach internet?
- Verify route table association with private subnets
- Check gateway's NAT rules are active
- Ensure VMs in private subnets have route to 0.0.0.0/0 via 10.0.1.4
Security Note
This configuration uses "permit any any" NSG rules for simplicity. In production:
- Restrict SSH to specific source IPs
- Implement more granular firewall rules
- Consider Azure Bastion for secure access
- Use Key Vault for credentials
Clean Up
terraform destroy
This will remove all created resources and stop billing.